Industrial Control Systems (ICS) are the “nervous system” of key sectors such as manufacturing and energy supply, and their network security directly determines the stability of production and even the safety of physical environments. However, many technicians encounter confusion when dealing with ICS security. Today, we will clear up some common but often overlooked points.
1. What is a Firewall? What is an Industrial Firewall? What are the Differences?
A firewall is a security system that uses both hardware and software technologies to create a protective barrier between internal and external networks. Information can only pass through the firewall if approved, thus blocking insecure elements from entering the internal network.
An industrial firewall is specifically designed for the control systems within industrial environments. The key differences include:
High reliability and low power consumption: Designed to meet the harsh conditions of industrial applications.
Protocol filtering: Filters industrial control system protocols, supporting commonly used communication protocols in ICS.
White-list access control: Supports a white-list strategy to manage which entities can access the system.
Pre-configured protection rules: Comes with rules and detection mechanisms for various ICS controllers and communication protocols.
Traffic and communication rate limitations: Supports centralized platform management, allowing for more effective monitoring.

2. What are Patches? What Are the Main Types of Patches?
A patch is a software update designed to address issues, bugs, or vulnerabilities in existing software. Patches cannot operate independently and must be integrated with the original software.
The main types of patches include:
Critical vulnerability patches: These address vulnerabilities that could be exploited by malicious code and should be applied immediately.
Security update patches: These patches fix major security vulnerabilities and should be patched as soon as possible.
Optional high-risk vulnerability patches: These address vulnerabilities specific to certain applications and should be applied carefully.
Functionality update patches: These patches update system or software functionality and can be applied based on need.
Obsolete patches: Patches that are expired, ignored, or already blocked, and do not require fixing.
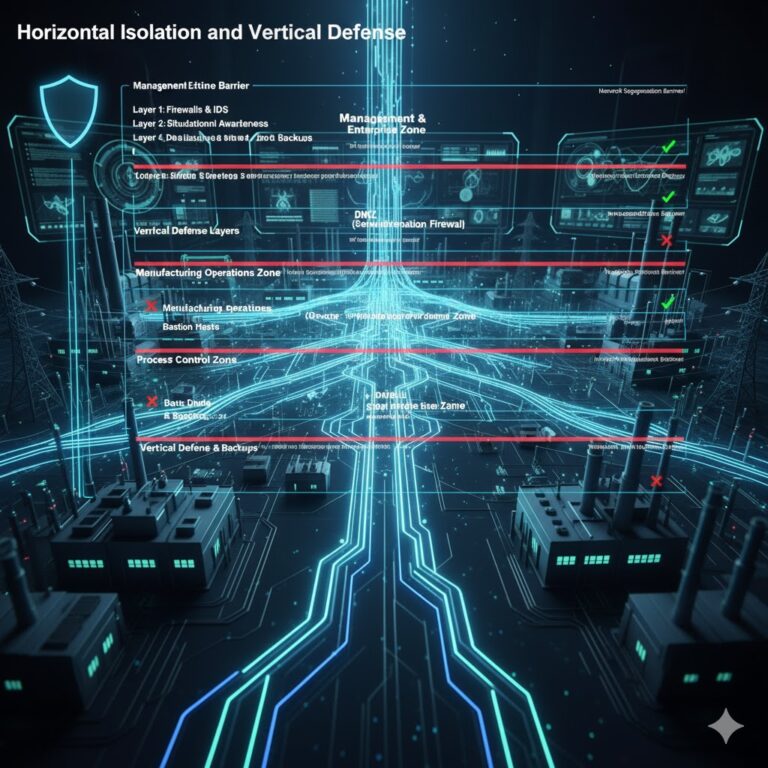
3. What Does “Horizontal Isolation and Vertical Defense” Mean in Control System Security?
Horizontal Isolation refers to dividing the control system into different sections, units, or regions. This creates clear boundaries, making it easier to implement security measures. In the event of a virus infection or external attack, it helps to isolate the threat within a smaller section.
Vertical Defense involves deploying different defense strategies at various levels of the control system network. This includes using firewalls, intrusion detection systems, situational awareness systems, bastion hosts, and disaster recovery measures.
4. What are Some Unsafe Practices in Industrial Control System Maintenance?
Common unsafe behaviors include:
Arbitrarily adding communication interfaces or network connections.
Using simple or default usernames and passwords.
Unrestricted use of removable media.
Lack of supervision in critical areas such as control rooms or server rooms.
Inadequate security measures during system maintenance or remote management.
Failure to apply necessary patches or vulnerability fixes for operating systems and software.
Not installing or updating antivirus software in time.
Lack of security audit technology and experience.
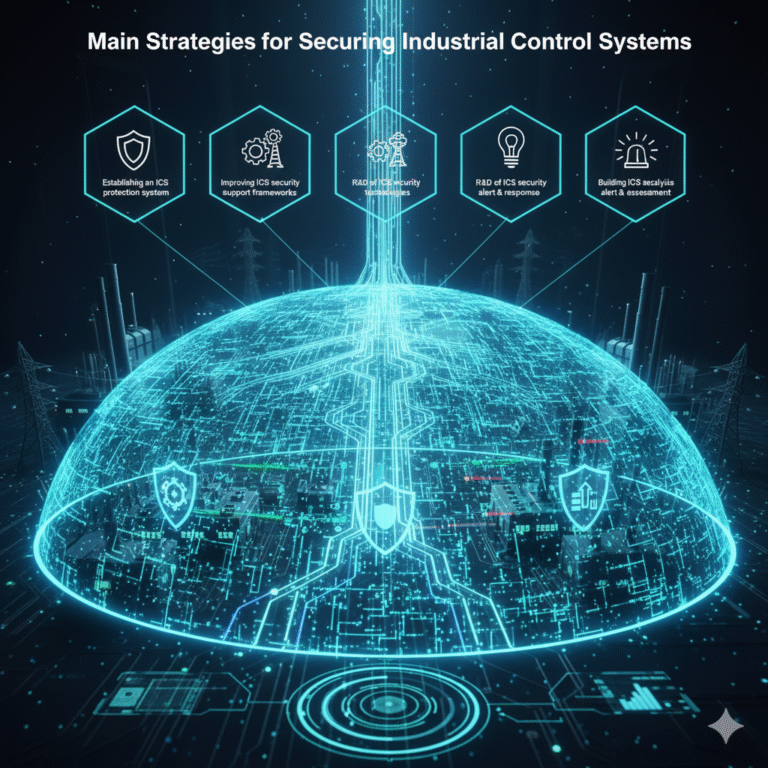
5. What Are the Main Strategies for Securing Industrial Control Systems?
Key strategies for ICS security include:
Establishing an ICS protection system: Strengthen the foundation of ICS security by implementing robust protective measures.
Improving ICS security support frameworks: Develop and refine the security measures surrounding ICS.
Enhancing the research and development of ICS security technologies and products: Invest in innovative solutions for ICS security.
Building ICS security alert and response mechanisms: Develop systems that can quickly identify and respond to security threats.
Conducting ICS vulnerability analysis and risk assessment: Regularly assess the security posture of ICS and take preventive actions.
Boosting active defense capabilities in cyberspace: Employ proactive defense measures to counter cyber threats.
6. What Are the Main Functions of an Industrial Control System Firewall?
An industrial control system firewall differs from a traditional firewall in several ways. Its main functions include:
Deep packet inspection for industrial control system protocols such as OPC, Modbus, and DNP.
White-list access control: Only allows pre-approved devices and systems to communicate with the ICS.
Network security control: Implements strict security policies for ICS networks.
Protection against common internet attacks: Offers pre-configured protection against a variety of network threats.
Learning, alerting, and blocking modes: Supports adaptive security measures based on system behavior.
